
It’s been a rough year for WordPress. The world’s most popular blogging system has been the repeated target of hackers intent on exploiting weaknesses among its tens of thousands of plugins. Some attempts have been wickedly successful. Others pathetically parasitic but ultimately benign. The story begins fourteen months ago, and lessons can be learned from its array of mischief and cyber cunning.
It’s only a question of whether or not those dependent on vulnerable WordPress plugins will heed the warnings and become proactive about their cyber security in time for the next attack.
The WordPress Phishing Fiasco
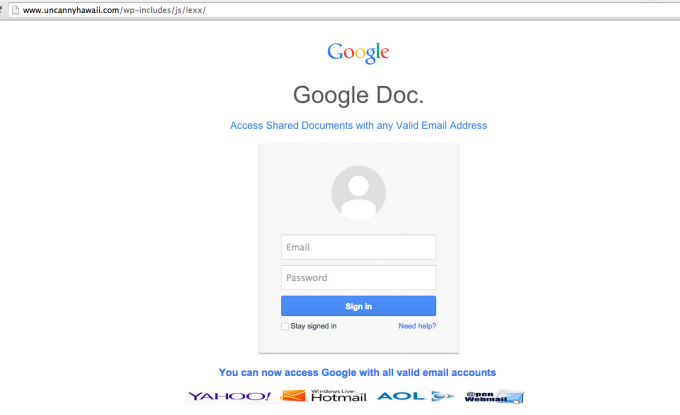
Phishing with help from Compromised WordPress Sites
Roughly 12,000 WordPress installations were found to be hosting malware in February, 2014, according to cyber security news source CSO. The phishing attacks launching from these add-ons targeted Apple and PayPal accounts by encouraging users to login and provide credit card information. After the prompt screen was closed users were sent to the actual Apple or PayPal websites. Fix updates were immediately deployed, but the weaknesses of web-based development platforms had been exposed for the world to see.
Cyber-security professionals and hackers-for-hire have been busy assisting developers better protect their sites ever since. It seemed so far so good leading all the way into 2015. But while WordPress-based users and developers began to start sleeping easy, opposing agents were simply laying low to gear up for the next generation of CMS-focused attack.
The SEO Plugin Breach

Common WordPress Malware Infections
Things got taken up another level in March of this year when hackers performed a successful Blind SQL Injection on an SEO plugin used by over 14 million people. According to news site SearchEngineLand this sort of attack leads to a full-on data breach, in that unauthorized users are able to manipulate and control the data itself. Additionally, hackers using the Blind SQL Injection tactic can slip just about any kind of malware or spam they want onto compromised websites.
It’s been a wake-up call to anyone and everyone with a tie to WordPress and her many, many plugins. One-fifth of the top one-percent most popular websites on the worldwide web use WordPress as their chosen content management system. Breaches in plugins are no small spectacle when global user activity is taken into account.
Experts consistently recommend users and businesses opt for comprehensive Internet security software specifically designed to monitor and evolve with the changing face of malware. It’s the first and most important step in proactively protecting against any cyber threat, let alone those which threaten the CMS your company or brand depends on for its existence.
Bad Actors
How To Scan Your WordPress Website For Hidden Malware
A somewhat less threatening but more newsworthy attack on WordPress plugins came in early April at the hands of hackers associating themselves with the militant group calling itself the Islamic State, otherwise known as ISIS. According to Forbes the FBI doesn’t actually think the cyber attackers are linked to the infamous Iraq and Syrian-based organization, but are merely sympathizers living elsewhere. The attacks, little more than implants of pro-ISIS, anti-West messages, were achieved by exploiting – you guessed it – weaknesses in WordPress plugins.
Good Solutions

HOW TO FIND AND CLEAN UP INFECTED WORDPRESS FILES OVER SSH
As mentioned earlier, protection against these sorts of CMS-based attacks starts with self-updating, 24-hour monitoring malware protection. Updates are essential. It’s often literally a race of minutes between coders and criminals when it comes to developing measures and countermeasures to the inherent weaknesses found in every sophisticated piece of software. WordPress and her many plugins are not an exception, it’s a wide world of mostly amateurishly guarded web-based services many tech business leaders take for granted. Don’t assume the protection exists already – take charge of it on your own.
The tough run-in with illicit activity on the part of WordPress over the last year has been an alarm bell for anyone getting too comfortable with their base-protected content management systems. Gear up to ensure your data and the data of your customers and clients isn’t compromised thanks to a weakness built deep into the code of a popular but amateurishly built plugin.



