
The Internet is full of threats. Phishers, malware, Trojan horses and other sneaky cyber crime techniques can devastate a business or an individual. While there are steps you can take if your data and identity is stolen, the best protection prevents attacks before your business or reputation is ruined. But what are the best preventative measures you can take so your data stays safe from cyber attacks? Here are some tips.
Emails:
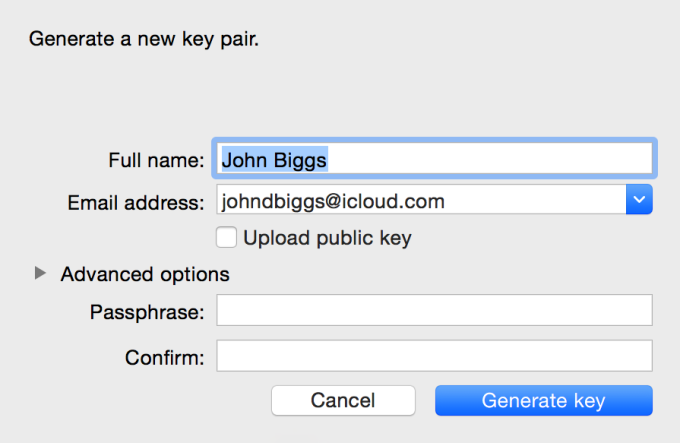
The Founder’s Guide To Email Security
Email viruses and malware were one of the first forms of cyber attacks, and though most people have become good at identifying them, email attacks still exist. Tips from the Department of Homeland Security on cyber attacks specifically instruct users not to click on any links within an email. Even if you think the link could be legitimate, one that promotes an offer or sale from a retailer, simply open a new tab on your web browser and visit the site directly. If you think the email is malicious, don’t open it at all.
Antivirus:
Don’t count on antivirus software alone to keep your data safe
One of the most powerful lines of defense against cyber attacks is a reputable antivirus and firewall. Antiviruses like Webroot, ESET and Bitdefender constantly monitor and filter threats from the net. A good antivirus like these ones will block email viruses and malware, monitor your online activity and even notify you when you attempt to enter unsecured sites. A reputable antivirus detects and flags threats before they are an issue. All the antiviruses above come in individual subscriptions or business subscriptions for multiple seats. If a business uses mobile devices such as tablets or 2-in-1 hybrids, many cyber security systems, like ESET even support a theft prevention service whereby a phantom account is provided for thieves. Once the phantom account is opened the camera on the device takes a picture of the thief. On the antivirus’s website you can report your computer stolen and locate it if the thief has accessed the phantom account.
Authentication:

How to Protect Your Small Business Against a Cyber Attack
Two-factor authentication is one of the most effective ways to secure your accounts. When enabled on a site or account, when you enter your username and password, the site will redirect and ask for an authentication code. The authentication code is sent to your email, texted via smartphone or shows up on the authentication app. Of course it depends on which authentication services you use. Google provides an app, as does Apple. A third party authenticator, Authy, is also a trusted alternative.
For Businesses:

5 Ways Hackers Can Get Into Your Business
Businesses face unique challenges in the cyber security market. Much of the time, even small companies react slowly while hackers change their strategies constantly for desired results. Many businesses are shocked that their weakest point is their employees. Many security breaches occur because employees partake in activities that are not work related while on company computers. Whether they use a weak password, click on an email link or enter information into a fraudulent site from a work computer, there are many risks. Businesses can eliminate these risks with company policies that discourage employees from personal activities on work computers and servers. If a business utilizes cloud servers, the security around them is commonly more robust than what could be found for localized servers. While security experts are costly for small businesses, a good one can save a business the hassle and heart ache of a cyber attack.




