
There are only so many cautionary tales you can read about the very public, very unfortunate victims of DDoS attacks before you decide that hmm, no, you can’t let that happen to your business. Whether it’s the Blizzard gaming servers getting nailed for an entire weekend, Dutch banks being rocked so hard by a teenage attacker everyone assumed it was Russia doing the attacking, or a cryptocurrency exchange going down while margin traders do the social media version of screaming their heads off, there is no shortage of DDoS horror stories abounding, and no shortage of reasons to start taking your own protection seriously.
It can be hard to know where to begin when it comes to getting distributed denial of service attack protection, however. Typing DDoS protection into your search engine without knowing the features you need is like going to Amazon and typing in shoes – you’re going to want to narrow it down a little.
Here are a few protection essentials to look for in prospective services.
The Brains

What the WannaCry Attack Means for IoT Security
Distributed denial of service attacks can be crafty little buggers. When aimed at the application layer they’re designed to cause mayhem using requests that look legitimate, ones that use up as many server-side resources as possible. This makes them incredibly difficult to differentiate from actual traffic. Nonetheless, mitigation services shouldn’t be blocking traffic with broad strokes in order to prevent attacks because if legitimate users are denied access by DDoS protection, then in a way that DDoS attack has succeeded without its attack traffic getting through.
Instead, DDoS protection needs to be armed with deep packet inspection and granular traffic analysis capabilities in order to truly differentiate actual traffic from attack traffic. This will likely include progressive challenges, ones that seek to avoid impacting user experience at all costs. Further, with attackers now hiding attacks in encrypted traffic, DDoS protection services need to be able to rapidly unencrypt, analyze, and re-encrypt traffic to ensure nothing malicious is sneaking in.
The Brawn

Think Your Business Is Secure? Think Again [Infographic]
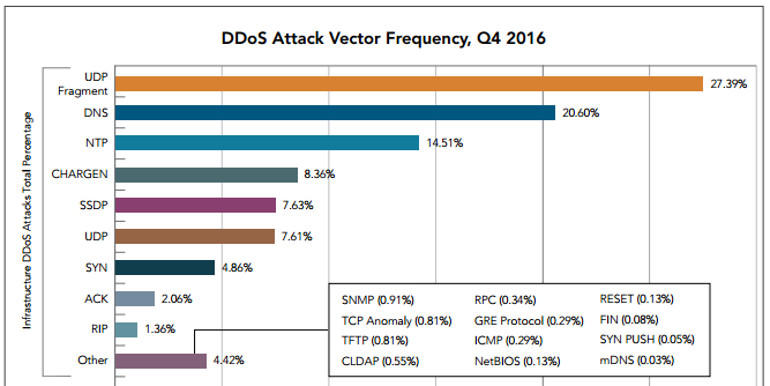
If you follow DDoS news at all, you’ve assuredly seen headlines about the booming, bruising network-layer attacks coming from IoT botnets. It’s now commonplace for websites to be smashed with hundreds of gigabits per second, with sizes going all the way up to the 1+ Tbps attacks seen levied against the Dyn DNS server, GitHub and an unnamed target of a 1.7 Tbps attack. As such, mitigation services need to have a network of scrubbing servers and data centers capable of handling at least 500 Gbps. Anything less and the Internet of Things could very well be coming for you.
The Speed
Final Nightmare: Online Gaming And The Never-ending DDoS Threat
Every minute counts when it comes to DDoS attacks. For many websites and services any downtime at all translates to users that can’t log in or access a service, which translates to frustrated users whose loyalty can be seriously impacted in the long-term. Further, even for attacks that cause just short bursts of downtime, the time spent dealing with the fallout of the attack is much longer behind the scenes, with communications staff struggling to keep up with inquiries from users, IT or security staff scrambling to ensure there are no intrusion attempts accompanying the attack, and other employees stymied by backend processes being downed.
Distributed denial of service attacks need to be stopped before they can start. Not stopped quickly, not minimized, but blocked altogether. To ensure that attack attempts cannot get through, you need a DDoS protection service that guarantees a time to mitigation that comes in under ten seconds. This should be outlined in your service level agreement.
In the Clouds

Top Tech Innovations For Business Success
The distributed denial of service situation is unruly, always evolving and never abating. Choosing the right protection against this onslaught is one of the most important cybersecurity moves you can make, and all it takes to get the right protection is keeping a few must-haves in mind. With cloud-based distributed denial of service protection that boasts the three essentials listed above, you will be on your way to never becoming a DDoS cautionary tale. In today’s internet landscape, that is undoubtedly one of the best things you can be.



