
Cybersecurity incidents are always on the rise. Both large and small organizations fall victim to cyber-attacks which are becoming more sophisticated. Using artificial intelligence (AI), attackers have tools that can easily gain unauthorized access to systems. AI cyberattacks can also dodge traditional security controls.
Understanding cybersecurity

Cybersecurity activities aim at protecting computer systems from unauthorized access to data and damage from cyber-attacks. Having a reliable information security system is a score for organizations. However, due to the ever-evolving threat landscape, implementing effective cybersecurity is a challenge.
Today, most companies rely on Software as a service (SaaS) models to store sensitive data and confidential information. This helps them shift security to other parties. They also implement frameworks such as NIST to help them identify attacks, detect and respond to threats, and protect and recover from successful attacks.
Common Cyberattacks
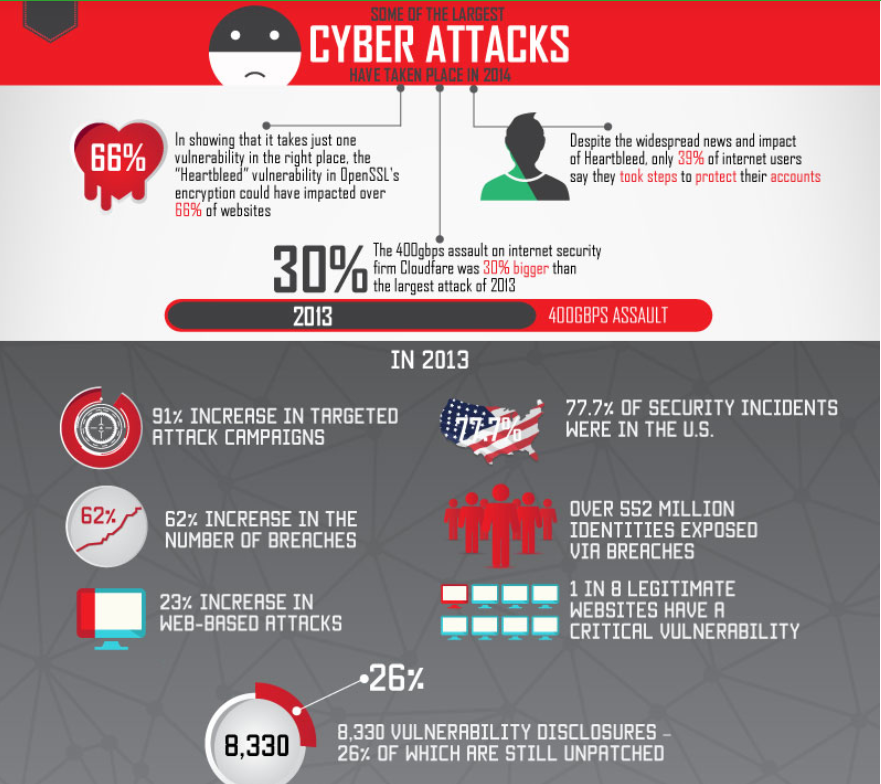
The most common types of cyberattacks include malware, Distributed Denial of Service(DDoS), ransomware, and social engineering.
Malware
Malware includes trojan horses, worms, and viruses. It also involves the use of spyware tools to steal data from computer systems. For instance, key loggers can send keystroke data to cybercriminals. Attackers usually employ malware to damage and gain access to sensitive information.
Malware is spread through networks and file vectors. For example, on the internet, users are tricked into clicking malicious links that compromise their security.
Distributed Denial of Service (DDoS) Attack.
This attack floods request to networks which can in turn cause network systems to crash. Attackers intend to make it difficult for users to access a service. DDoS is achieved by overloading access to applications, networks, services, devices, and servers. Systems are overwhelmed with requests, and hence they cannot offer services as intended.
Ransomware
Cybercriminals utilize this attack to extort victims. Ransomware disrupts functions within organizations by mostly encrypting essential data. Cybercriminals then demand payment to decrypt the information. This type of cyber attack is costly to organizations.
Besides an expensive ransom, cybercriminals may blackmail the organization again. Organizations also incur huge losses and even lose assets. Trying to recover from lost functionality and operations has also proven costly.
Social Engineering
Social engineering is a manipulative way an attacker uses to gain access to systems. They use the weakest link in cybersecurity – human resources. Social engineering involves a lot of sophisticated techniques to get data. The most common one is phishing. Attackers trick users into taking actions that compromise security measures
This is by creating trust with users and tricking them into obtaining crucial information to access their systems and data. Attackers may impersonate a legitimate entity and manipulate users to give out personal information such as passwords.
Consequences of Cyber Attacks

Cyber-attacks have unwelcome ramifications in organizations. Attacks on information systems result in financial loss, especially under a ransomware attack. Unauthorized access to financial information such as credit card information will lead to loss of money.
The cost of correcting cyber attacks is high. Organizations incur high prices in the recovery and replacement of affected systems. Breach of security laws increases regulatory and compliance charges. Organizations could suffer regulatory fines or sanctions following cyber attacks.
Cyber attacks also result in reputational damage. Organizations will lose consumer trust and scare away present and potential customers to competitors. Poor public relations will further ruin the reputation, and this will affect other connected companies.
Importance of Cybersecurity

Cyber attacks are not only growing, but they are also costly. The cost of cyber risk is prohibitive if proper security measures are not integrated into organizations. Organizations need to protect their systems and save on recovery and replacement costs.
It is possible to uphold a positive reputation and retain customer trust in business using reliable cybersecurity measures and standards. Implementing proper cybersecurity solutions is vital to eliminate potential cyber-attacks on sensitive information within organizations. This will increase efficiency and minimize costly law suits.
Enhancing Cybersecurity in Organization

Organizations should focus on promoting security awareness to minimize the risks of cyberattacks. They must implement practical security solutions such as intrusion detection systems to detect and report abnormalities in the system. One effective way to ensure this is the case is to turn to experts offering cybersecurity compliance services, in order to get advice on strategies to take in the interest of system security. This should be coupled with other security technologies to give a business a fighting chance against any potential cyber threats.
Recruiting qualified cybersecurity personnel is also critical in organizations. Such individuals will offer a better analysis of information systems and implement appropriate policies to protect the company against malicious attacks.
The organization should offer training to employees on the risks of cyberattacks. Employees must be educated on the dangers of social engineering and schemes used by attackers to acquire sensitive information.
Organizations should also formulate policies, standards, and frameworks regarding cybersecurity. This should help them to know how to deal with cyberattacks. They should also comply with regulations and cybersecurity laws.
Wrap up

Cybersecurity is essential for organizations and individuals seeking to protect their devices, networks, data, and sensitive information against unauthorized access. With the advancement in technology, sophisticated attacks now exploit unseen vulnerabilities in systems.
It is therefore crucial for organizations to implement effective cybersecurity controls and measures to protect against such attacks. Information security personnel must spearhead effective security measures to guard information systems against the different forms of cyberattacks.
Cybersecurity compliance services with security measures will also reduce the impact of security incidents in organizations.




