In the digital age, cyber threats are constantly evolving. Hackers are becoming more sophisticated, and businesses are facing greater risks than ever before. To stay ahead of these threats, organizations
10 Ways AI and Automation are Redefining Cyber Threat Responses
The world of cybersecurity is constantly evolving as attackers develop new ways to exploit systems. To keep up, businesses are adopting advanced technologies like artificial intelligence (AI) and machine learning
The Role of Managed Security Service Providers in Modern Cyber Defense
Keeping up with growing numbers of cyberattacks is no easy task. Many security teams are understaffed, dealing with increasingly complex infrastructure. As a result, they are overtaxed, and many organizations
8 Steps to Enhance Your Organization’s Security Posture
In a world where cyber threats are growing daily, safeguarding your organization’s information and assets has never been more important. From data breaches to ransomware attacks, organizations of all sizes
How To Deal With Vandalism at Your Business
Vandalism is a nightmare for small business owners and property managers, often resulting in unexpected repair costs and interruptions to daily operations. Protecting your business from vandalism is crucial to
Why Sensitive Data Discovery is Vital for Compliance
Many organizations have noticed recently that compliance regulations are getting tighter (and imposing very expensive fines). Laws like the GDPR in Europe, and similar regulations in California and some other
Choosing the Right VDR Provider A Comprehensive Guide for Secure and Efficient Data Room Management
The use of cloud storage for efficient data management is rapidly increasing in the global corporate sector. Studies revealed that almost 60% of all business world data is stored and
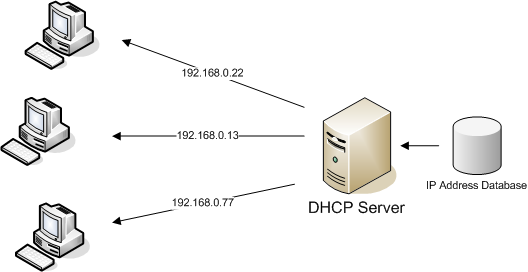
Understanding DHCP Port: An Essential Component of Network Configuration
In computer networking, the Dynamic Host Configuration Protocol (DHCP) plays a crucial role in automatically assigning IP addresses to devices on a network. DHCP relies on specific ports to operate