Technology is at the heart at every business, regardless of what sector they operate in. Whether you’re a self-employed sole trader, a company director or an entrepreneur, you’ll rely on
The Benefits of Working in Cybersecurity
The field of cybersecurity is growing rapidly, and there is a high demand for qualified professionals. In 2023, the global cybersecurity market is expected to be worth $223.9 billion, and
Which Web Hosting Services Accept Bitcoin and Cryptocurrencies and Why Is It Important?
Nowadays, many companies allow payments in bitcoins. This cryptocurrency, which is the virtual currency designed to function as a medium of exchange, is decentralized and be aware that there’s no
The Facial Scan Could Be a Problem in Online Businesses
Facial scan could be a problem in online businesses for a number of reasons. Privacy concerns: Facial scans collect a lot of personal data, including biometric information that can be used
Common IT Security Issues
When it comes to your network’s IT security and protecting sensitive data and vital information, learn some of the most common issues. Cybersecurity is a subject on almost every business
VPN Can Change Your Perspective of Browsing
In an age in which hacking and cyber attacks are becoming increasingly common, finding ways to securely surf the web is becoming vital. Indeed, not only can these attacks and
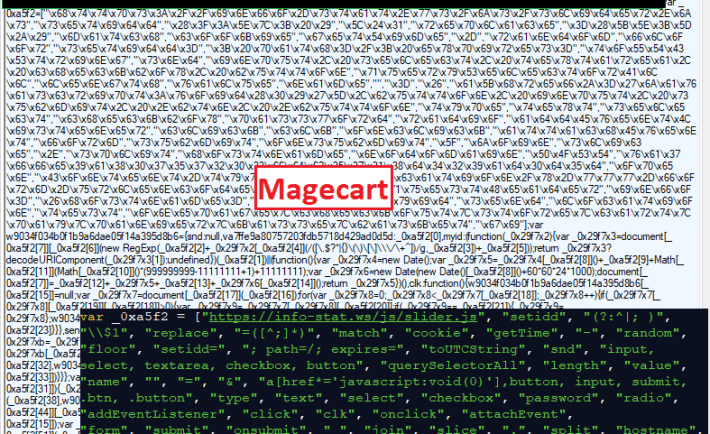
How to Protect Sensitive Information on Your E-Commerce Website
If you have an e-commerce website, you need to identify Magecart as a massive security threat to your online assets. A recent analysis found that nearly 37% of websites have
More Than A Web Host: What Can The Cloud Do For You?
The Cloud has become somewhat of a buzzword over the last decade or so. Coming to describe just about every online service at some point or another, it can be