It’s a constant game of tug-of-war between those who want to infiltrate the internet and those who want to protect it. As a business especially, having outdated or inferior security
How To Develop A Mobile Application Users Will Love
Here are some critical points on how to develop a mobile application users will love: Start with a clear understanding of your users’ needs. What are they trying to accomplish with
Hoping to Hire Top Cybersecurity Talent?
Students that are interested in pursuing careers in the STEM fields (science, technology, engineering, management) will have near-guaranteed employment prospects if they study cybersecurity methodologies. Data breaches and hacking attacks
Outsourcing to Protect Your Company
When it comes to security and health matters, it’s imperative that your business complies with laws and regulations. A hack or loss of data can cost your company massive amounts
Prepare For The Future: Online Education and the Cloud
As the world moves closer to total and infinite connectivity, it’s important to know how this actually works. People love to reference “the cloud,” but many of us are unsure
Cybersecurity Trends We’ll See In 2018
Each brand new year brings lots of new and emerging cybersecurity threats. So, as 2018 is almost here, it’s time to look ahead to the coming year to see what
It’s Time To Go Into Security Overdrive!
You might not worry too much about security in your business but you should because the issue with security has never been higher and more apparent. Indeed, Global ransomware costs
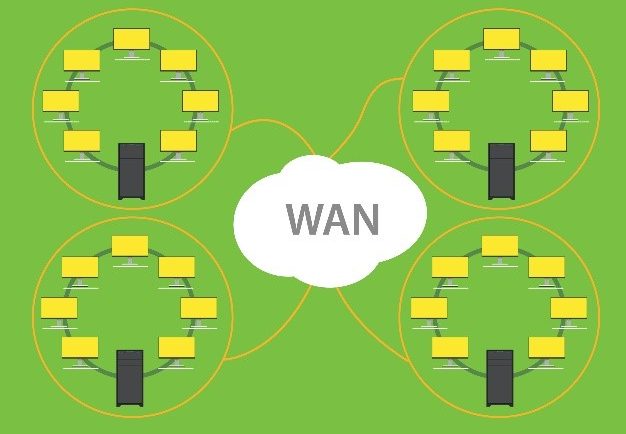
Why You Can’t Forget to Monitor Your WAN
Often, business environments devote resources to LAN network monitoring to reduce congestion and recognize failing components, both of which are significant obstacles for productivity and performance. Yet, while IT managers