When people hear the terms “cyber-espionage” or “hacker”, they assume someone in a pullover hoodie, locked in his room, writing a bunch of script in a command prompt, all so
Company Drug Testing: What Are the Laws and Should You Do It?
If you are running a business and are unsure whether to drug test your employees, click here to learn what is legal along with whether you should do it. The
Google Is Going to Eliminate Chrome Extensions Which Abuse Users’ Information
Good news for us: Google will soon tighten his security and protect user rights by eliminating the extensions of Chrome that need personal information and use it for unknown purposes.
Shielding IoT Against Security Breach
The Internet of Things (IoT) is an interconnected array of electronic devices linked by the Internet, through which they transmit and receive data. The original “thing” was a Coca Cola
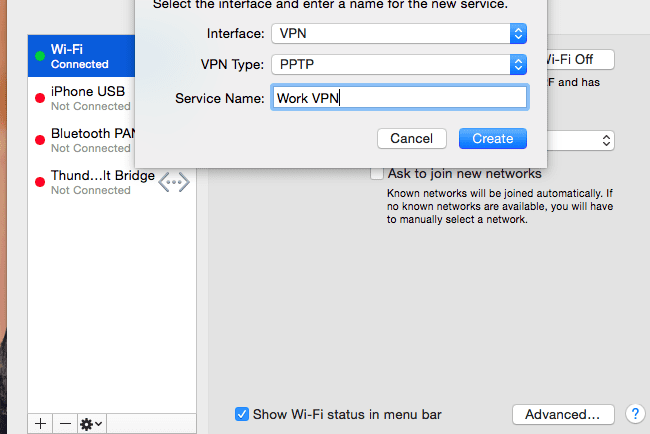
How Do You Set Up a VPN on Mac – Manual Guide and Provider Suggestions?
If you have decided to use a VPN on your Mac? Then it is time to set up one. If you have not yet chosen any VPN yet then you
What Should You Do When You Get Mysterious Phone Calls?
We’ve all been there. The cellphone or landline phone rings, and we pick up the phone, but the voice on the other end isn’t familiar. It’s someone claiming to be
4 Key Benefits Of Having A Secured Website
A secured website brings tons of benefits not only to online users, but to website owners also. Privacy and data protection should be prioritized at all times to prevent identity
Don’t Let A Crisis Take Your Brand Down
There’s one essential truth about businesses; namely, things will at one point or another go wrong. It’s in the nature of business interactions and processes to face unexpected events. Of