Keeping up with growing numbers of cyberattacks is no easy task. Many security teams are understaffed, dealing with increasingly complex infrastructure. As a result, they are overtaxed, and many organizations
Understanding DHCP Port: An Essential Component of Network Configuration
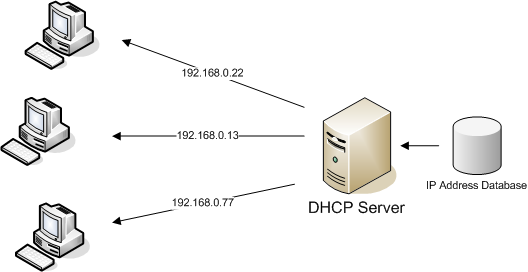
In computer networking, the Dynamic Host Configuration Protocol (DHCP) plays a crucial role in automatically assigning IP addresses to devices on a network. DHCP relies on specific ports to operate
Best Oracle Data Integration Tools: A Comprehensive Overview
In today’s fast-paced digital landscape, businesses heavily rely on data to make informed decisions and stay ahead of the competition. Oracle, a leading provider of database management systems, plays a
Outdated IT Is The Biggest Cause Of Business Downtime, Not Hackers
We tend to think of downtime as something that happens when a hacker figures out how to compromise company systems. And while this is a risk, the biggest threat is
It’s Time To Go Into Security Overdrive!
You might not worry too much about security in your business but you should because the issue with security has never been higher and more apparent. Indeed, Global ransomware costs
How Liquid Web Hosting Is Helping Developers #BuildSomethingBrilliant
This post was written by me through an activation with HireInfluence on behalf of Liquid Web. Although I received compensation for participating in the campaign, all thoughts and opinions are
5 Reasons to Opt for Linux Web Hosting
For a rookie webmaster, choosing a web hosting plan may be a challenging task. What web hosting environment to choose is an especially critical decision to arrive at. FreeBSD, Microsoft,
10 Gigabit Ethernet & The Future of Networking
The rise of cloud computing is a bit like that of a space shuttle taking off. When the rocket engine and its propellants fire up, the shuttle lifts slowly off